Strong passwords are essential to protecting your business and personal online account.
However, in some cases, a strong password may not be enough to deter cybercriminals from assuming your online identity and accessing your business or personal data.
Dive into this guide on two-factor authentication because it offers practical advice on securing your online accounts against cyber threats.
Using two-factor authentication (2FA) will better safeguard your online accounts and the online accounts of your employees.
Before we discuss two-factor authentication in detail, here are three password best practices you’ve probably heard many times before. They bear repeating.
1. Use a different password for every online account.
2. Store your passwords in a password manager instead of a spreadsheet or document. Popular password applications include Keeper and 1Password.
These vendors also offer business versions for sharing passwords among team members.
3. Use strong passwords. Your password manager has the option to generate these.
Strengthening Login Security With Two Factor Authentication
Two-factor authentication (2FA) is also known as 2-step verification (2SV). In general, 2FA means that after entering your username and password (the first factor), you are provided with a one-time use code that needs to be entered if you are logging into an online account from an unfamiliar device — or if too much time has passed since you last logged in.
Consider using the two-factor authentication option of any of your online apps. Examples of popular cloud applications that offer 2FA are Google Workspace, Microsoft 365, Salesforce, LinkedIn, and Amazon.
Apps like Duo and Jumpcloud provide centralized 2FA management. One login gives a user access to multiple apps via Single Sign-On (SSO).
Even though it may seem logical that having 2FA on an account reduces the importance of using strong passwords, it’s still a best practice and a good habit to use strong passwords on all online accounts — regardless of whether they have the additional protection of 2FA.
2FA is a subset of MFA (multi-factor authentication). With MFA, a third factor could be used, although requiring more than two factors to access an account is uncommon because it’s inconvenient for users.
1. Email Two Factor Authentication
Email is the most convenient form of 2FA since emails can be accessed from various devices.
While much stronger than a password, email 2FA can be exploited by a phishing attack, as demonstrated in this video.
2. Text Two Factor Authentication
SMS text 2FA is more secure than email 2FA since the verification code can normally only be accessed from one place — your mobile phone.
Of course, if you are trying to log in to an email account such as Google Workspace or Office 365, an emailed verification code is a ‘Catch-22’ and, therefore, not a viable option.
If you don’t happen to have your mobile phone with you, additional options are covered below.
There have been reported cases where someone’s mobile SIM card has been spoofed or swapped so the hacker could receive a copy of the 2FA code sent out as a text message.
3. Phone Call 2FA
A telephone call to a mobile or landline number is equivalent in security to a text message. An automated voice reads out a verification code.
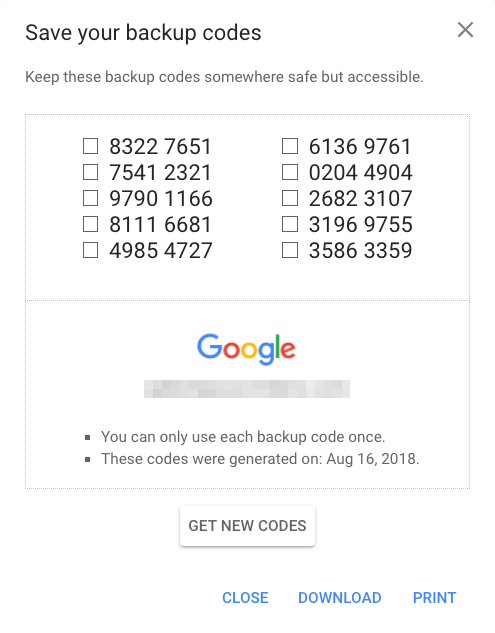
4. Backup Codes
Backup codes are designed to be printed and carried in a wallet or stored securely at home. For example, a code can be used for verification when a mobile phone is unavailable.
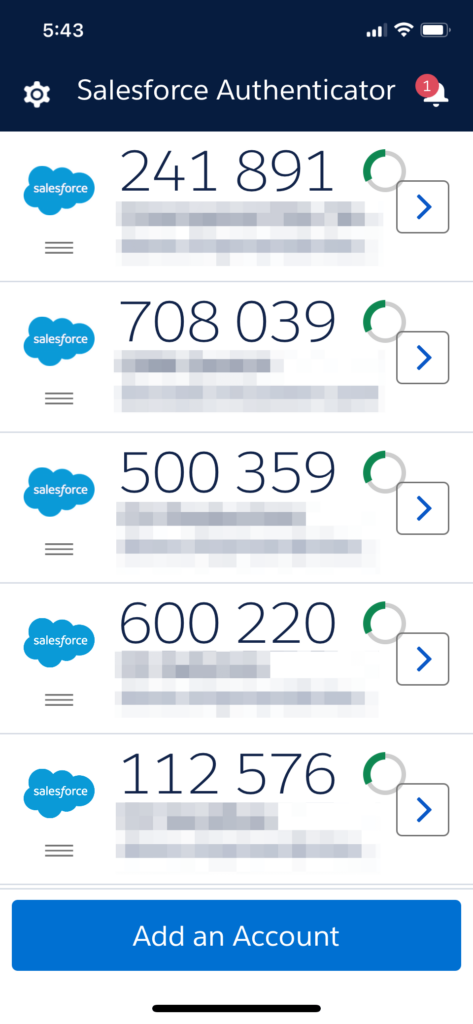
5. Mobile Authenticator Application (Software Token)
A stronger level of 2FA is using a mobile authenticator app like the ones offered by Salesforce, Google, and Microsoft.
Using location services to set up trusted locations such as ‘office’ and ‘home’ reduces the possibility of device spoofing.
6. Physical Security Key (Hardware Token)
A physical security key is the strongest 2FA online account protection level and the best phishing attack prevention.
The key is a small device that can be added to a keychain and plugged into a computer, tablet, or mobile device. This is the most phishing-resistant account protection available. It is also the most expensive to roll out to every user.

The Yubikey from Yubico works with many popular applications.
Google has a similar product to Yubico’s called the Titan Security Key. This key works with Google Workspace and Google Cloud. It has a Bluetooth connectivity option.
Password best practices coupled with two-factor authentication will make your and your employees’ online accounts more secure, better protecting their information.


