Digital credentials, such as usernames and passwords, connect you and your employees to business applications, email systems, and online services. Unfortunately, hackers know this—and that’s why digital credentials are among the most valuable assets traded on the Dark Web.
Not only are usernames and passwords for sale, but also for sale is Personal Identifiable Information (PII) such as phone numbers, addresses, and social security numbers. With this PII, cybercriminals can hack systems and impersonate you or your employees more easily.
Cybercriminals utilize the Dark Web to plan and exchange tools and information that enable and propel attacks against businesses of all sizes. But you can get the upper hand and understand if activities are being plotted against your business by getting informed about the leading indicators of an impending attack: leaked credentials.
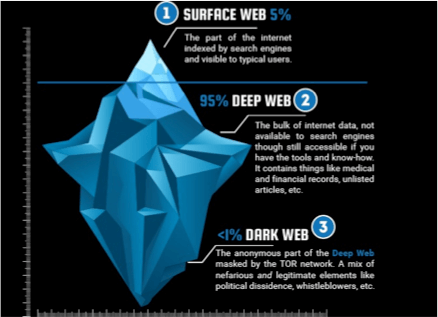
What is the Dark Web?
The Dark Web comprises digital communities hidden deeply on the Internet. Cybercriminals operate on the deep web, using protected forums and closed sites to buy and sell stolen identities and passwords. It is estimated that over 50% of all sites on the Dark Web are used for criminal activities, including the disclosure and sale of digital credentials. Unfortunately, companies that have had their credentials compromised and sold often are even aware of it until they have been hacked or informed by law enforcement. And then the damage is done.
Yes. This Can Happen to You
When your employees use their work email to access services and other third-party websites, such as those below, it only heightens your company’s vulnerability to a breach.
We all regularly read about large service providers such as Marriott or CapitaOne suffering massive data breaches. Those breaches can result in your company’s credentials finding their way to the Dark Web for sale to the highest bidder.
Remember, employees often use their company passwords to access
- Travel sites
- Social media
- Banking
- HR/Payroll

According to UpGuard, here are some of the most significant data breaches ever reported. Each of these data breaches impacted millions of people and provide different examples of how a company can be compromised or leave an extraordinary number of records exposed. You will recognize one or more of these as sites your employees may access with company credentials.
- Yahoo – 3 billion
- Marriott – 500 million
- Twitter – 330 million
- Linkedin – 165 million
- Adobe -153 million
- Anthem – 78 million
- Dropbox – 69 million
Compromised credentials are used to conduct further criminal activity
Remote Workers Elevate The Risk of Compromise
If the ongoing battle against cyber criminals was not enough, a new dimension of risk has been introduced with a transition to work-from-home employees.
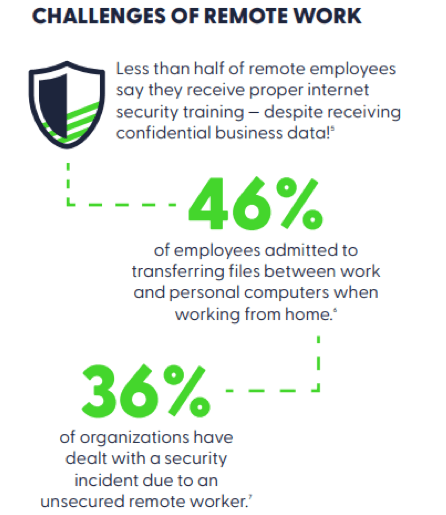
While remote work has allowed many businesses to continue operations, it also increases security challenges as employees remotely access the company network, files, and data. A company workstation is often unavailable, leaving employees to work from desktops or laptops. These computers are often not adequately protected against attacks, including viruses, malware, and phishing attacks.
Moreover, a company’s perimeter security protection does not monitor personal computers, which provides threat detection and prevention.
As a result, the risk of credentials being stolen is now greater than ever. And to make matters worse, employees often use the same password for multiple services, such as email login, social media, and business applications, thus increasing the potential damage from a single compromised credential.
How To Protect Your Business
Top Goals
- Reduce the risk of account takeover, business email compromise, and live hacking
- Improve password policy awareness and enforce company password policy
- Improved awareness of threat actors and dark web activity to help prevent stolen accounts resulting in financial damage
Step 1 – Get a Dark Web Scan Report Immediately
Our Dark Web report offers detailed visibility into your business accounts that are in circulation on the Dark Web, posting a risk of being used in an actual attack on your business. This scan will scan the dark web to see if your information has been compromised in known data breaches.
The resulting report will include the email address, credential (unencrypted password), date the credential was stolen, and the source of the theft (i.e., breach). From there, you can alert and change.

Request a free Dark Web Scan Report ➡️
Step 2 – Enroll in a Dark Web Monitoring Service
The threat is ongoing and requires continuous detection of credential theft. Dark Web Monitoring is an affordable service to set up to constantly monitor the dark web to detect if your company is at risk due to exposed credentials.
With this type of real-time visibility, you stay one step ahead of the cyber criminals that want to take over your network, install ransomware and steal sensitive business data.
- Protect against a breach with early detection of compromised user credentials
- 24×7 monitoring of the dark web for stolen corporate credentials of your users
- Safeguard the personal credentials of highly-targeted executives and privileged users
- Immediate notification of compromised user credentials discovered on the dark web


