If you own or operate a company, one of the cyber threats you may be most worried about is employees falling victim to phishing attacks.
Phishing is a type of cyberattack that uses fraudulent emails or websites to trick users into revealing sensitive information, such as login credentials (username & password) or financial information. Some phishing emails have attachments that are payloads for malware.
According to the security awareness and training firm KnowBe4, “Business phishing emails are the most clicked [email] subject category globally.”
Phishing attacks cost U.S. companies hundreds of millions of dollars a year.
Businesses are prime targets for phishing activity, as business data is often more valuable to a bad actor than personal information. The average cost of a successful business phishing attack is millions of dollars.
Phishing scams are more sophisticated and more difficult to distinguish from legitimate emails than ever. In addition, malicious emails may use familiar-looking branding or logos — including those of your own company.
Despite increased sophistication, most phishing messages have telltale indicators that they may be a scam. Below are common signs of a phishing attempt.
If you receive an email from someone you don’t know or from a company you do business with that has an unusual tone or a strange greeting, be wary — it could be a sign of a phishing email.
Grammatical errors or misspellings
Many phishing emails still originate from countries where English is not an official language. As a result, you may receive an email that looks like it’s from a legitimate source but has poor grammar and spelling mistakes.
These emails are often sent by scammers, trying to trick people into giving them personal information or money. So be careful of these emails, and never click on any links or attachments from someone you don’t know.
Odd language and tone
Every email has a set of standard components. These include the subject, the sender’s name, the sender’s email address, the salutation, the body text, the signature, and the mailing address.
- The subject does seem consistent with the subject text in previous emails from the same vendor
- The sender’s email address contains a misspelled domain name
- If the salutation is impersonal, such as “Dear Client”
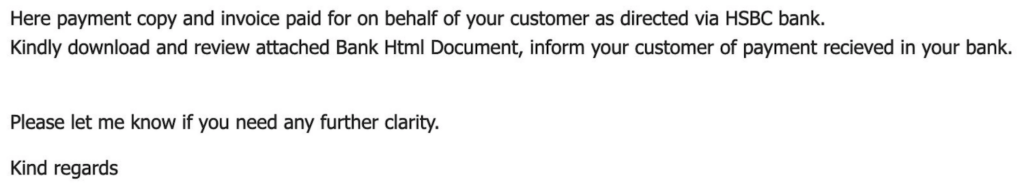
- The body text references a PDF attachment, but the attachment is HTML
- Words like “kindly” are used, which may indicate that the email originated outside the country
- The signature reads, “Sincerely, [brandname].”
- The mailing address — presented to appear compliant with the CAN-SPAM act — is not an actual address
If any of these components seems “off” or unusual, it’s worth a quick visual scan of the other elements.
No body text
To avoid detection by email filters, certain scammers are now making the body of the email one large graphic. This way, filters do not have any text to examine.
If you hover your cursor over the email body, you’ll see that it’s a single, clickable image. But do not click the image in the email.

Free offers like the above tend to be used more in direct-to-consumer emails rather than emails to work addresses. However, it may just be a matter of time before all-image emails end up in business account inboxes.
Phishing email calls to action
To profit, a criminal must ask the email recipient to take action. These malicious calls to action can have several different forms.
“Click this link”
You may get an email that asks you to click on a link to verify your account information or update your billing information.
The email may look like it’s from a legitimate source, such as your bank or another company with which you do business. But when you click on the link, the URL is for a fake website designed to steal your personal information.
Hover over the link before clicking it. The preview of the link may indicate a bogus URL.
“Open the attached file”
You may get an email with an HTML attachment that doesn’t look quite right.
When opened, the attachment runs a script that infects your computer.
“We’re closing your account – act now”
People can experience a quick emotional response to emails threatening to close one of their accounts.
This type of message is an email that threatens to close your account or take other action if you don’t respond within a specific timeframe.
A wire transfer request from an owner or executive
Sometimes referred to as ‘CEO Fraud,’ this type of phishing attack takes advantage of the fact that employees take quick action on what they believe to be a direct request from a company executive.
A hacker can take over an executive’s email account using a technique known as adversary-in-the-middle (AiTM). The cybercriminal can then send a phishing email to a junior-level employee from a legitimate email account.
There’s often a sense of urgency to the requests. For example, the fake sender may state, “I’m about to board a plane, and I need you to wire money to this vendor before I land.”
“We’re about to charge your account”
In a highly sophisticated phishing attack in late 2022, scammers were able to create invoices through PayPal’s API, which triggered phishing emails sent directly from PayPal’s email servers to customers.
Here is a LinkedIn post from investigative reporter Brian Krebs.
The scammers used the invoice’s legitimate “Seller note to customer” section to add a fake customer support number directed to their operation.
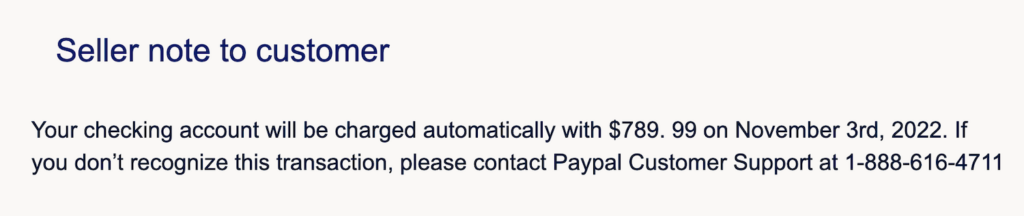
This scammer message also has subtle errors — a space before “99” in the dollar & cents amount and a lowercase “p” in the middle of the word “PayPal.” It’s essential to pause and take a look at minor details.
Consider the source
Some business email sources have a higher percentage of fake emails than others. Therefore, it can pay to be extra vigilant about messages from familiar originators.
Emails from your company’s HR department
According to KnowBe4, emails that appear to come from a company’s human resource department are the most common type of business phishing email.
Email subjects include “your performance evaluation is due” and “dress code changes.”
LinkedIn notifications
LinkedIn is the most impersonated brand by phishers.
These attacks replicate LinkedIn’s stylized email templates to get LinkedIn subscribers to click on phishing links to fraudulent sets, where there is a prompt to enter their credentials. Email subjects include “You appeared in 5 searches this week” and “Who’s searching for you online.”
Alerts from business productivity vendors
Since productivity apps from Google, Microsoft, and Zoom are popular in the workplace, these are common vendors for cybercriminals to imitate.
Protection from Phishing Attempts
The best way to protect yourself from a phishing attack is to get good at identifying anomalies in email messages. The same applies to texts (smishing) and phone calls (vishing).
Vishing Example
If you are traveling for business, watch out for a vishing attack in which you receive a call on your hotel room phone. The scammer says that it’s the front desk calling because there was a problem with your credit card. You are then asked to repeat the numbers on your card or provide a different credit card.
Smishing Example
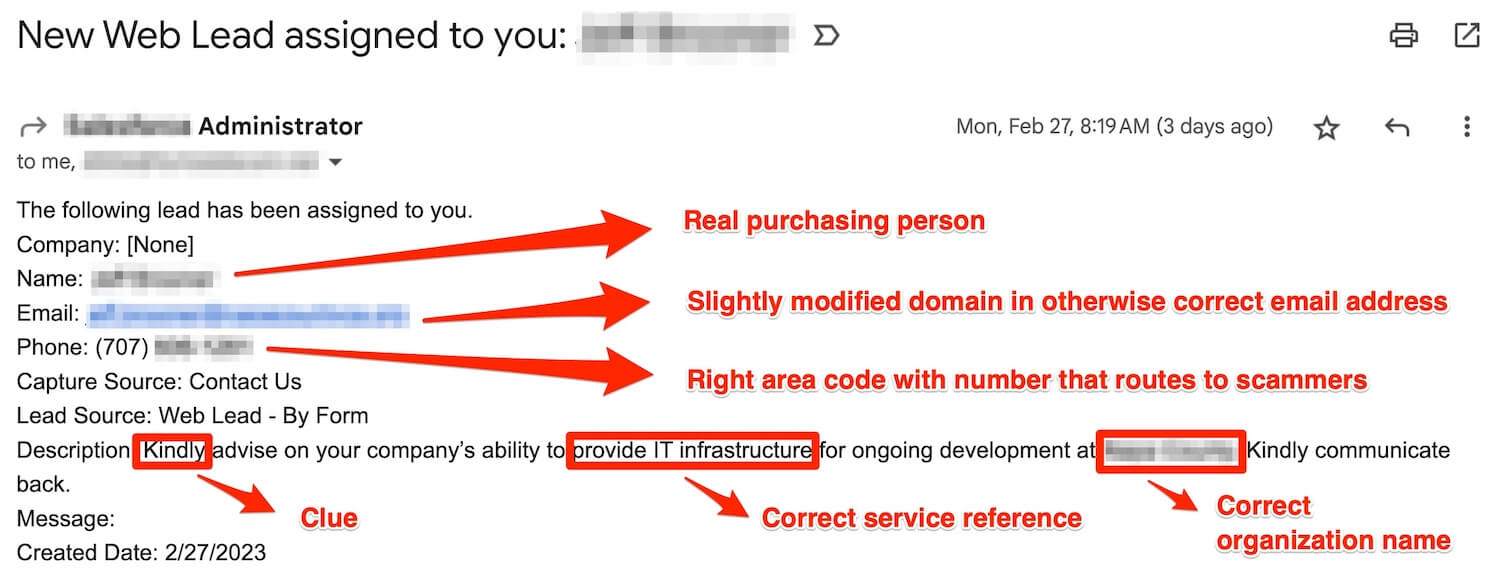
A two-step smishing attempt we recently saw started with a fake lead form submission.
Here are the details:
- The name is an actual purchasing person
- A fake email address (slight modification)
- A fake phone number with the right area code that routes to the scammers
- A personalized message appears to be written by an offshore scammer
- The caller ID is captured when the “lead” is called
- The caller’s phone number goes into the scammer’s smishing database
From there, the scammer can launch targeted, contextual smishing attacks.
What You As a User Can Do
Let’s get back to the topic of email. As a user, you can protect yourself from phishing attacks by being suspicious of unsolicited emails or links and verifying the sender’s identity before clicking links or opening attachments.
Sayings and thoughts to keep in mind include:
- Trust but verify
- If it seems too good to be true, it probably is
- Never give credentials or credit card information to someone who contacts you
- Careful if something merely important is being portrayed as urgent
- Compare an email’s customer support phone number with the number on the vendor’s website
- Take a few extra seconds to examine the details of how words are spelled and their casing
While it’s mainly up to each person to spot phishing indicators, your organization can help protect you by implementing email and web filtering solutions.
Email Provider Filtering
Business email providers like Google and Microsoft have built-in phishing detection. If the filters miss a phishing attempt, email users can report what they believe to have been a phishing email.
Secondary Filtering
The second line of technical defense is third-party software that gives employees inline notifications about first-time senders and AI-based alerts that an email may be a phishing attempt. Our Defensor product provides this functionality.
If you suspect a phishing email, be sure to contact your helpdesk. Unlike common IT support requests like printer jams, reporting this issue quickly is critical so that others within your organization can be alerted.